
Connector Type
Configuration of bintec secure IPSec clients |
The bintec secure IPSec client™ is called up with Start -> Program -> FEC Secure IPSec Client -> Secure Client Mode. Configuration of the bintec secure IPSec clients™ is performed with the assistant. At first launch of the bintec secure IPSec client™ the new assistant profile starts automatically.
Under Connection Type, select Company Network Connection over IPSec.

Connector Type
Enter a name for the profile, e.g. Head Office .

Profile Name
In the next step of the assistant, you must select a connection medium over which to set up a connection to the Internet. In our example, the LAN (over IP) selection is used as the bintec secure IPSec client™establishes no direct Internet access but uses an Internet access router.

Connection Medium
In the option Access data for Internet service providers the address at which the VPN gateway is accessible from the Internet, e.g. vpngateway.bintec-elmeg.com , is saved under user name.

User Name
Then, Main Mode is used as Exchange Mode. If main mode is used, data for setup of the IPSec Phase1 is already transmitted in encrypted form, in contrast to aggressive mode. For PFS group, as already at the VPN gateway, the DH Group 2 (1024 Bit) is selected and the option Use IP Compression enabled.
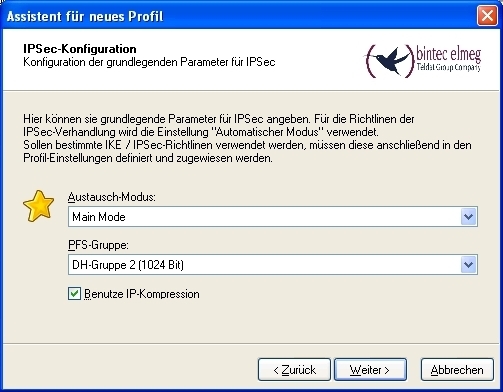
IPSec Configuration
As authentication of the bintec secure IPSec client™ occurs with certificates, no pre-shared key is saved. The Type of Local Identity is set to ASN1 Distinguished Name .

Pre-shared key
In this example, a dynamic VPN IP address is assigned to the VPN IPSec client. IKE Config Mode must also be enabled.

IKE Config Mode
In the final step, the firewall of the bintec secure IPSec client™ is configured. If the client is directly connected to the Internet, the firewall should be enabled.

Firewall
After the assistant for setup of a new VPN tunnel is run, the certificate (PKCS#12 file) of the first VPN client must be copied on this computer. Then, the user certificate is selected in menu Configuration -> Certificate -> Add of the bintec secure IPSec client™.
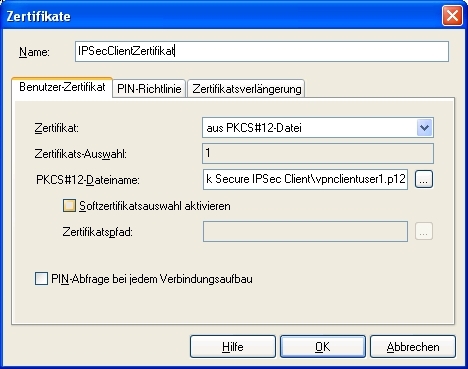
Certificates
After this, certain adjustments are still required in the VPN connection profile.
In menu Configuration -> Profile -> Edit -> IPSec Settings the predefined IKE Policy RSA Signature and the IPSec Policy ESP - AES128 - MD5 are selected .

IPSec Settings
The previously-created certificate policy is selected in menu Configuration -> Profile -> Edit -> Identity. The certificate/certificate profile saved here is used for authentication at VPN IPSec tunnel setup.

Identity
| Copyright© Version 01/2020 bintec elmeg GmbH |