Stateful Inspection Firewall (SIF)
|
|
The next subsystem that the packets move through, after the NAT, is the Stateful Inspection Firewall. As
the status of the WAN interface is "not trustworthy" no initial requests may be placed in the default settings for this
interface, instead only corresponding requests from "trustworthy" interfaces (initially all LAN interfaces) will be
answered. Initially, the requests continue to be blocked, this time from the SIF.
A rule that enables this access to be an exception to output behaviour must be created.

|
Note |
|
With the Stateful Inspection Firewall the rule applies that packages that are permitted due to a rule
cannot be subsequently forbidden, and vice versa. If necessary, the sequence of the rules that have been passed through
must be observed!
|
In our example, all protocols and ports for access from the WAN to the IP address of the Internet gateway
(192.168.2.254) must be enabled. The required interfaces and the service summary "any" have already been predefined,
only the Internet gateway IP address requires definition.
Go to the
Firewall->Addresses->Address
List->New
menu.
Proceed as follows:
-
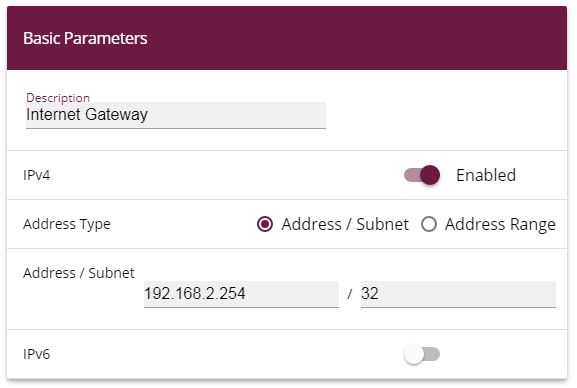
Enter a
Description such as
Internet Gateway
.
-
Under
Address /
Subnet enter the IP address of the Internet gateway
192.168.2.254
and the sub-network
32
.
-
Click
OK to confirm your
settings.
As a new rule access from the WAN interface to the IPv4 address of the Internet gateway is defined for
every service and for all protocols.
Go to the
Firewall->Policies->IPv4
Filter Rules->New
menu.
Proceed as follows:
-
Select a
Source such as
WAN_GERMANY - TELEKOM ENTERTAIN
.
-
Select the
Destination =
Intern Gateway
.
-
Select the
Service
any
.
-
Leave
Action
Access
.
-
Click
OK to confirm your
settings.
A list of all configured IPv4 filter rules is displayed in the
Firewall->Policies->IPv4
Filter Rules menu.
| Copyright© Version 01/2020 bintec elmeg GmbH |
|